NoVirusThanks Unloaded Module Viewer allows you to analyze running processes unloaded modules to assist in malware location.
Download
NoVirusThanks Unloaded Module Viewer allows you to analyze running processes unloaded modules to assist in malware location.
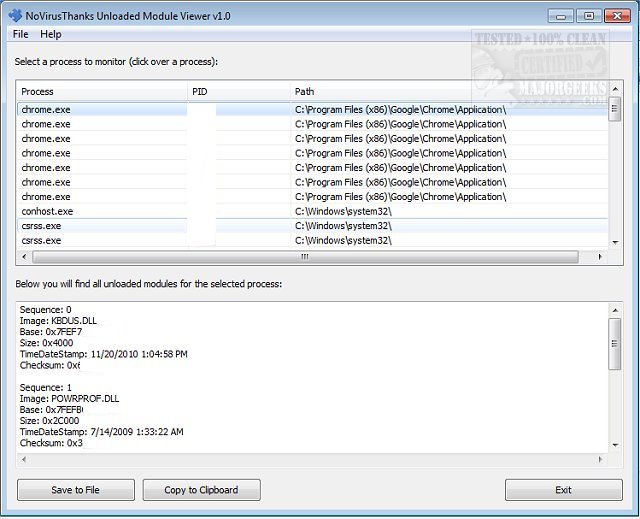
NoVirusThanks Unloaded Module Viewer enumerates and lists Portable Executable (PE) modules (.DLL, .CPL, .EXE, etc.) that during the life of a process have been dynamically unloaded. When the Windows PE loader (with APIs such as FreeLibrary/LdrUnloadDll) unloads a module, specific information is cached as a snapshot by NTDLL (NT Layer DLL) within the process address space. This cached information can come in handy when investigating potential malware activity. This cache consists of the last 64 modules unloaded and provides pertinent details like the module name/size, load address, timestamp, and checksum.
Once launched, NoVirusThanks Unloaded Module Viewer immediately displays all active processes. All the details are provided from a single window UI from which you have access to each processes name, ID and full file path, from there you can expand the details by clicking on a target entry which will then display the dynamically unloaded modules. All details provided can be easily copied to the clipboard or saved to a log file. The information provided by NoVirusThanks Unloaded Module Viewer does not require an active debugging session on any target process, unlike the WinDbg -LM (list loaded and unloaded modules) command.

Download

