NoVirusThanks OSArmor monitors and blocks suspicious process behavior and is aimed at preventing infections by malware, ransomware, and other common threats. For complete protection consider Malwarebytes.
Download
NoVirusThanks OSArmor monitors and blocks suspicious process behavior and is aimed at preventing infections by malware, ransomware, and other common threats. For complete protection consider Malwarebytes.
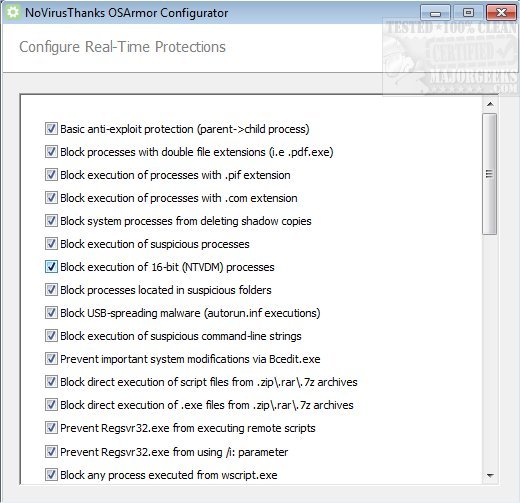
It works by analyzing parent processes and prevents scenarios like MS Word running cmd.exe or powershell.exe and can prevent ransomware from deleting file shadow copies via vssadmin.exe. It also blocks processes that have double file extensions like invoice.pdf.exe for example, as well as blocking malware spread by USB.
NoVirusThanks OSArmoris simple to use requiring no configuration but you can choose specific areas for monitoring through the Configurator by simply checking/unchecking a selection. It is designed to run silently in the background while protecting your system without eating up a large amount of memory. This tool is capable of blocking even those threats not detected by your selected security solution making it an additional defense layer against malware, ransomware, etc.
NoVirusThanks OSArmor Features:
Basic Anti-Exploit
-Analyze parent processes and child processes blocking exploit payloads
Protect MS Office Apps
-Prevent WINWORD.EXE or EXCEL.EXE from executing malicious processes
Monitor Applications
-Monitor Adobe PDF Reader, MS Office, OpenOffice, Web Browsers, etc.
Block USB Malware
-Prevent execution of processes started via autorun.inf from USB devices
Block Command-Lines
-Block processes with command-line strings commonly related to malware
Protect Shadow Copies
-Block system processes (vssadmin.exe, etc.) from deleting shadow copies of files
Block File Download
-Block specific command-lines related to download of remote files
Block .COM & .PIF
-Block execution of processes with .COM or .PIF obsolete file extensions
Filter System Processes
-Block wscript.exe, mshta.exe, etc., if they match our rules of bad behavior
Block Bcedit.exe
-Prevent important and critical system modifications from Bcedit.exe
Block Schtasks.exe
-Block the execution of schtasks.exe (commonly used by malware)
Block Bitsadmin.exe
-Prevent Bitsadmin.exe from downloading (/download) remote files
PowerShell Rules
-Block execution of encoded or malformed commands via PowerShell
Svchost & Explorer
-Block suspicious behaviors related to Svchost.exe and Explorer.exe
Block RegisterXLL()
-Prevent calling of Application.Excel RegisterXLL() via command-line
Block Remote Scripts
-Prevent Regsvr32.exe or Mshta.exe from loading remote scripts

Download

