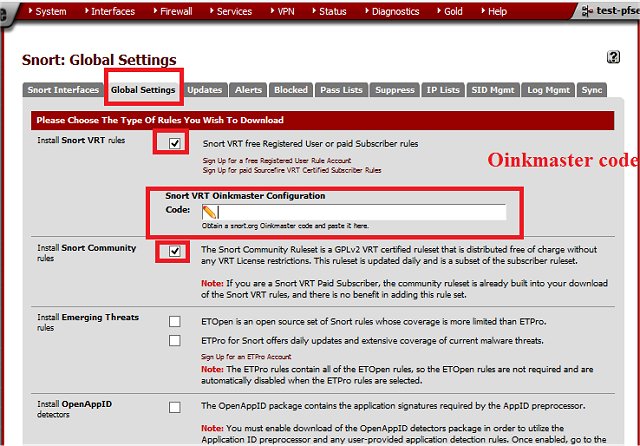
Snort, an Open Source network intrusion prevention system, has released version 3.10.1.0. It is designed for real-time traffic analysis and packet logging on IP networks, making network security accessible to users beyond just IT professionals and corporate entities. Unlike a firewall that mainly blocks or allows traffic based on set rules, Snort functions as both an Intrusion Detection System (IDS) and Intrusion Prevention System (IPS). It analyzes network traffic against predefined rules to detect threats such as malware and port scans. When used as an IPS, Snort can actively drop malicious packets, but its primary role is threat detection and logging.
Snort is versatile and scalable, equipped with a robust rule-based system that is continuously updated by the Snort community and Cisco, allowing it to keep pace with evolving threats. It requires a command line interface for operation, although there are web-based GUIs available, albeit with a steeper learning curve. Users are encouraged to start by familiarizing themselves with the command line interface and experimenting with its various modes: Sniffer Mode for real-time monitoring, Packet Logger Mode for data recording, and Network Intrusion Detection Mode for comprehensive security.
Extended Information
To further enhance your understanding and utilization of Snort, consider these additional aspects:
1. Community Support: The Snort community is an invaluable resource for both new and experienced users. Engaging with forums and participating in discussions can provide insights into best practices, troubleshooting, and rule creation.
2. Custom Rules: One of Snort’s strengths is the ability to create custom rules tailored to specific network environments. This flexibility allows organizations to adapt their security posture to the unique risks they face.
3. Integration with Other Tools: Snort can be integrated with other security tools and platforms for enhanced functionality, such as Security Information and Event Management (SIEM) systems, which allow for centralized logging and more advanced threat analysis.
4. Regular Updates: Staying current with Snort updates is critical for maintaining security. Regularly check for new releases and updates from the Snort community to ensure you have the latest threat definitions and features.
5. Learning Resources: Leverage comprehensive learning materials, including official documentation, online tutorials, and community-led training sessions. These resources can help you effectively configure and manage Snort.
6. Performance Monitoring: As your network grows, monitor Snort’s performance to ensure it can handle increased traffic without compromising on detection capabilities. Consider hardware upgrades or optimized configurations if you notice performance issues.
By understanding and leveraging these aspects, users can effectively utilize Snort as a powerful tool in their cybersecurity arsenal, ensuring robust protection against a variety of network threats
Snort is versatile and scalable, equipped with a robust rule-based system that is continuously updated by the Snort community and Cisco, allowing it to keep pace with evolving threats. It requires a command line interface for operation, although there are web-based GUIs available, albeit with a steeper learning curve. Users are encouraged to start by familiarizing themselves with the command line interface and experimenting with its various modes: Sniffer Mode for real-time monitoring, Packet Logger Mode for data recording, and Network Intrusion Detection Mode for comprehensive security.
Extended Information
To further enhance your understanding and utilization of Snort, consider these additional aspects:
1. Community Support: The Snort community is an invaluable resource for both new and experienced users. Engaging with forums and participating in discussions can provide insights into best practices, troubleshooting, and rule creation.
2. Custom Rules: One of Snort’s strengths is the ability to create custom rules tailored to specific network environments. This flexibility allows organizations to adapt their security posture to the unique risks they face.
3. Integration with Other Tools: Snort can be integrated with other security tools and platforms for enhanced functionality, such as Security Information and Event Management (SIEM) systems, which allow for centralized logging and more advanced threat analysis.
4. Regular Updates: Staying current with Snort updates is critical for maintaining security. Regularly check for new releases and updates from the Snort community to ensure you have the latest threat definitions and features.
5. Learning Resources: Leverage comprehensive learning materials, including official documentation, online tutorials, and community-led training sessions. These resources can help you effectively configure and manage Snort.
6. Performance Monitoring: As your network grows, monitor Snort’s performance to ensure it can handle increased traffic without compromising on detection capabilities. Consider hardware upgrades or optimized configurations if you notice performance issues.
By understanding and leveraging these aspects, users can effectively utilize Snort as a powerful tool in their cybersecurity arsenal, ensuring robust protection against a variety of network threats
Snort 3.10.1.0 released
Snort is an Open Source network intrusion prevention system capable of performing real-time traffic analysis and packet logging on IP networks.