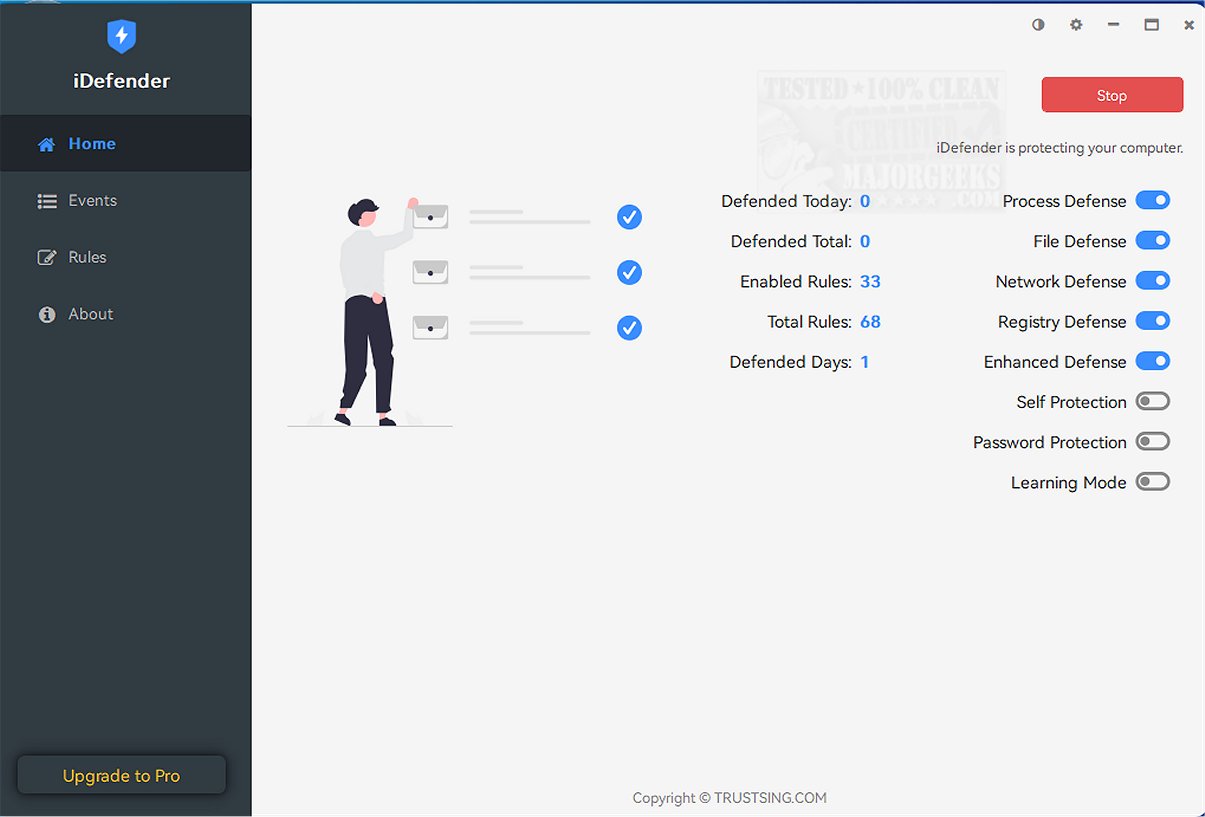
iDefender version 5.2.0.0 has been released, marking an important advancement in home security solutions. This innovative software integrates an Intrusion Prevention System (HIPS) with Real-time Endpoint Detection and Response (EDR), providing comprehensive protection for personal devices against a wide range of cyber threats.
Key Features of iDefender
1. Ransomware Protection: iDefender proactively combats ransomware by detecting and blocking attacks as they happen, protecting critical files from malicious encryption. Its advanced monitoring capabilities ensure that unauthorized encryption attempts are swiftly identified and thwarted.
2. Advanced Threat Mitigation: The software is designed to defend against complex cyber threats, including advanced persistent threats (APTs). iDefender employs cutting-edge techniques to block various attack vectors, such as shellcode injection and unauthorized remote access, which are commonly exploited by cybercriminals. It specifically targets vulnerabilities in documents and file-less attack methods to neutralize threats that could bypass traditional defenses.
3. OS Hardening: iDefender enhances system integrity by hardening the operating system and application environment. It effectively manages persistence mechanisms and high-risk behaviors, thereby reducing the potential attack surface and increasing the overall security posture of the system.
4. Blocking Unauthorized Access: With a strong focus on privacy and data security, iDefender implements multiple layers of protection. It employs techniques such as file hiding and access control to minimize the risk of data breaches and leaks, ensuring that sensitive information remains confidential.
5. Productivity Enhancement: In addition to security, iDefender is designed to boost user productivity by optimizing system resource management. It blocks unnecessary processes during system startup, preventing resource drain and maintaining optimal performance, allowing users to focus on their tasks without interruptions.
Conclusion
For those seeking robust protection against a multitude of cyber threats while ensuring a smooth user experience, iDefender is an outstanding choice. This powerful software provides significant protection against ransomware, sophisticated cyber threats, and exploitation attempts, alongside a suite of other critical security features. Users can rely on iDefender to keep their devices safe and resilient in an ever-evolving digital landscape, offering peace of mind in the face of increasing cyber risks.
Future Developments: As cyber threats continue to evolve, iDefender will likely undergo further enhancements and updates to adapt to new vulnerabilities and attack methodologies. Continuous development and user feedback will be essential in ensuring that iDefender remains at the forefront of cybersecurity solutions for home users
Key Features of iDefender
1. Ransomware Protection: iDefender proactively combats ransomware by detecting and blocking attacks as they happen, protecting critical files from malicious encryption. Its advanced monitoring capabilities ensure that unauthorized encryption attempts are swiftly identified and thwarted.
2. Advanced Threat Mitigation: The software is designed to defend against complex cyber threats, including advanced persistent threats (APTs). iDefender employs cutting-edge techniques to block various attack vectors, such as shellcode injection and unauthorized remote access, which are commonly exploited by cybercriminals. It specifically targets vulnerabilities in documents and file-less attack methods to neutralize threats that could bypass traditional defenses.
3. OS Hardening: iDefender enhances system integrity by hardening the operating system and application environment. It effectively manages persistence mechanisms and high-risk behaviors, thereby reducing the potential attack surface and increasing the overall security posture of the system.
4. Blocking Unauthorized Access: With a strong focus on privacy and data security, iDefender implements multiple layers of protection. It employs techniques such as file hiding and access control to minimize the risk of data breaches and leaks, ensuring that sensitive information remains confidential.
5. Productivity Enhancement: In addition to security, iDefender is designed to boost user productivity by optimizing system resource management. It blocks unnecessary processes during system startup, preventing resource drain and maintaining optimal performance, allowing users to focus on their tasks without interruptions.
Conclusion
For those seeking robust protection against a multitude of cyber threats while ensuring a smooth user experience, iDefender is an outstanding choice. This powerful software provides significant protection against ransomware, sophisticated cyber threats, and exploitation attempts, alongside a suite of other critical security features. Users can rely on iDefender to keep their devices safe and resilient in an ever-evolving digital landscape, offering peace of mind in the face of increasing cyber risks.
Future Developments: As cyber threats continue to evolve, iDefender will likely undergo further enhancements and updates to adapt to new vulnerabilities and attack methodologies. Continuous development and user feedback will be essential in ensuring that iDefender remains at the forefront of cybersecurity solutions for home users
iDefender 5.2.0.0 released
iDefender is a cutting-edge security solution designed for home use, offering both an Intrusion Prevention System (HIPS) and Real-time Endpoint Detection and Response (EDR). This integrated system protects against potential threats, ensuring the safety and integrity of your devices by actively monitoring and responding to suspicious activities.