HTTP Toolkit version 1.20.1 has been released, enhancing its ability to automatically intercept HTTP and HTTPS traffic from a wide range of clients, including popular web browsers like Chrome and Firefox, various command-line interface (CLI) tools, and back-end programming languages such as Node.js, Python, and Ruby.
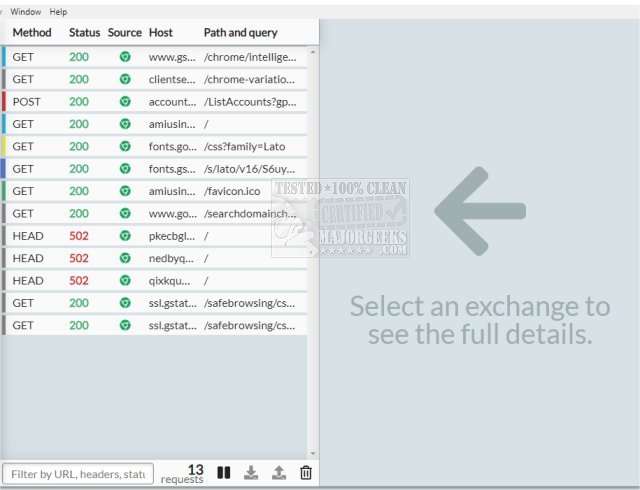
The toolkit serves as an HTTP(S) proxy for platforms lacking automatic integrations and is compatible with standard HTTP requests from virtually any language or tool. Users can easily sift through intercepted traffic, as the toolkit highlights essential components such as content type, status, and source. Additionally, users can search for specific messages based on URL, status, or headers, enabling them to locate relevant traffic quickly. Detailed examination of each request or response is facilitated by inline explanations and documentation from Mozilla Developer Network (MDN).
The toolkit boasts powerful features for inspecting message bodies, including syntax highlighting and auto-formatting for various data types like JSON, HTML, JavaScript, and hex, thanks to the integration of the Monaco editor from Visual Studio Code. Users can also pause and edit live HTTP traffic, allowing for precise modifications to requests such as target URL, method, headers, or body content. Furthermore, HTTP Toolkit enables manual responses to incoming requests and allows users to control the responses being sent back.
Key features of HTTP Toolkit include:
- Cross-platform compatibility (Linux, Mac, Windows)
- Comprehensive interception integrations
- Essential HTTP debugging functionalities
- Manual HTTP mocking and request rewriting capabilities
In summary, HTTP Toolkit 1.20.1 is a robust tool for developers and testers looking to streamline the process of intercepting and manipulating HTTP/S traffic, providing essential features for effective debugging and traffic management.
Future updates may further enhance its capabilities, potentially introducing more advanced features like enhanced analytics, user interface improvements, or expanded protocol support to meet the evolving needs of developers in a fast-paced digital landscape
The toolkit serves as an HTTP(S) proxy for platforms lacking automatic integrations and is compatible with standard HTTP requests from virtually any language or tool. Users can easily sift through intercepted traffic, as the toolkit highlights essential components such as content type, status, and source. Additionally, users can search for specific messages based on URL, status, or headers, enabling them to locate relevant traffic quickly. Detailed examination of each request or response is facilitated by inline explanations and documentation from Mozilla Developer Network (MDN).
The toolkit boasts powerful features for inspecting message bodies, including syntax highlighting and auto-formatting for various data types like JSON, HTML, JavaScript, and hex, thanks to the integration of the Monaco editor from Visual Studio Code. Users can also pause and edit live HTTP traffic, allowing for precise modifications to requests such as target URL, method, headers, or body content. Furthermore, HTTP Toolkit enables manual responses to incoming requests and allows users to control the responses being sent back.
Key features of HTTP Toolkit include:
- Cross-platform compatibility (Linux, Mac, Windows)
- Comprehensive interception integrations
- Essential HTTP debugging functionalities
- Manual HTTP mocking and request rewriting capabilities
In summary, HTTP Toolkit 1.20.1 is a robust tool for developers and testers looking to streamline the process of intercepting and manipulating HTTP/S traffic, providing essential features for effective debugging and traffic management.
Future updates may further enhance its capabilities, potentially introducing more advanced features like enhanced analytics, user interface improvements, or expanded protocol support to meet the evolving needs of developers in a fast-paced digital landscape
HTTP Toolkit 1.20.1 released
HTTP Toolkit offers automatic interception of HTTP and HTTPS traffic from most clients, including web browsers like Chrome and Firefox, almost all CLI tools, and back-end languages (Node.js, Python, Ruby, and more).