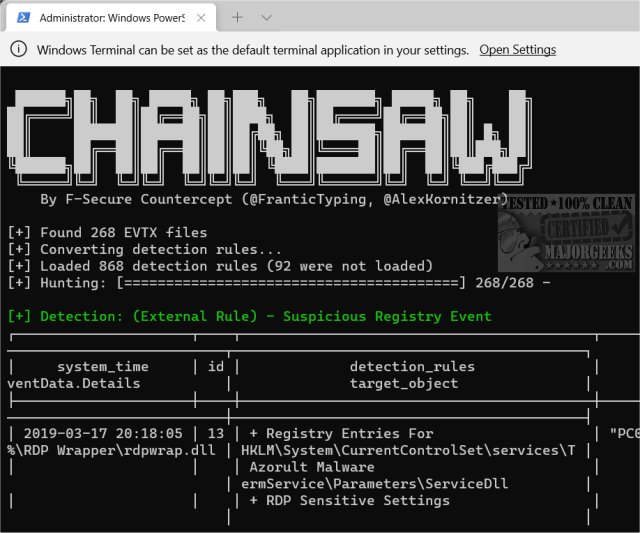
Chainsaw version 2.13.0 has been released, enhancing its capabilities for advanced users to efficiently search and analyze Windows Event Logs. This powerful tool serves as a 'first-response' mechanism, enabling quick identification of potential threats within event logs. Key features of Chainsaw include the ability to search and extract records based on event IDs, string matching, and regex patterns, as well as hunting for threats using both Sigma detection rules and custom built-in detection logic.
Chainsaw is designed for speed, being developed in Rust and utilizing the EVTX parser library by OBenamram, which contributes to its rapid performance. Additionally, it supports document tagging through the TAU Engine Library and allows output in various formats, including ASCII tables, CSV, and JSON.
This software is specifically tailored for advanced users who are familiar with Command Prompt, making it particularly valuable for technicians, system administrators, and IT professionals. For example, users can execute commands such as `./chainsaw hunt evtx_attack_samples/ --rules sigma_rules/ --mapping mapping_files/sigma-mapping.yml` to see how the program operates.
In addition, Chainsaw is an essential tool for cybersecurity efforts, especially for those looking to bolster their incident response capabilities. It empowers users to conduct thorough investigations into security incidents by providing them with the tools needed to sift through vast amounts of log data quickly and effectively.
For those interested in similar topics, resources for clearing event logs and interpreting Event Viewer logs for Check Disk operations are also available, helping users maintain system integrity and security. As cybersecurity threats continue to evolve, tools like Chainsaw are crucial for proactive monitoring and response strategies
Chainsaw is designed for speed, being developed in Rust and utilizing the EVTX parser library by OBenamram, which contributes to its rapid performance. Additionally, it supports document tagging through the TAU Engine Library and allows output in various formats, including ASCII tables, CSV, and JSON.
This software is specifically tailored for advanced users who are familiar with Command Prompt, making it particularly valuable for technicians, system administrators, and IT professionals. For example, users can execute commands such as `./chainsaw hunt evtx_attack_samples/ --rules sigma_rules/ --mapping mapping_files/sigma-mapping.yml` to see how the program operates.
In addition, Chainsaw is an essential tool for cybersecurity efforts, especially for those looking to bolster their incident response capabilities. It empowers users to conduct thorough investigations into security incidents by providing them with the tools needed to sift through vast amounts of log data quickly and effectively.
For those interested in similar topics, resources for clearing event logs and interpreting Event Viewer logs for Check Disk operations are also available, helping users maintain system integrity and security. As cybersecurity threats continue to evolve, tools like Chainsaw are crucial for proactive monitoring and response strategies
Chainsaw 2.13.0 released
Chainsaw allows advanced users to search and hunt through Windows Event Logs rapidly.