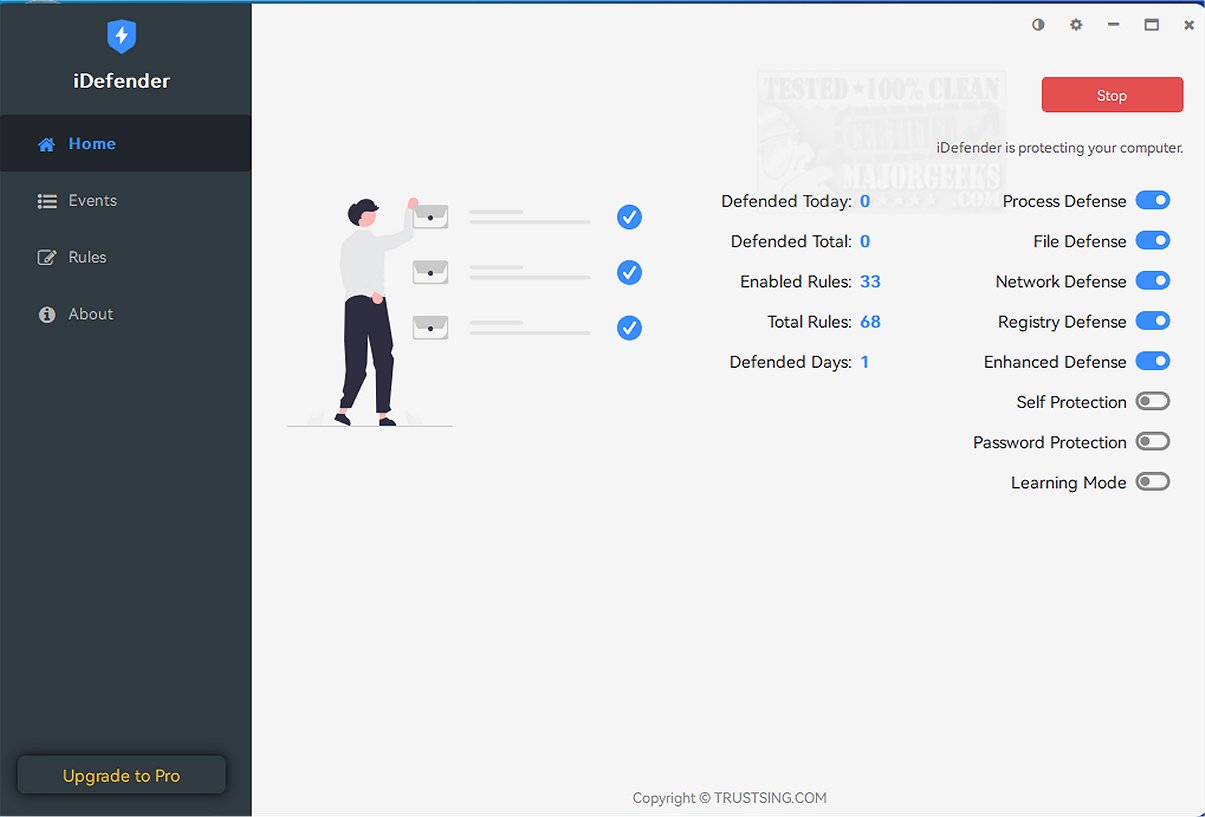
iDefender is a state-of-the-art security software tailored for home users, now available in version 5.2.2.0. It combines an Intrusion Prevention System (HIPS) with Real-time Endpoint Detection and Response (EDR) to deliver a robust defense against various cyber threats. This integrated solution actively monitors device activities and responds to potential security incidents, ensuring users' devices remain safe and their data secure.
Key Features of iDefender
1. Ransomware Protection: iDefender excels at combatting ransomware attacks. It detects and blocks these threats in real-time, protecting critical files from malicious encryption attempts. Its advanced detection mechanisms allow it to monitor for suspicious activities that may indicate unauthorized encryption, ensuring that valuable data remains uncompromised.
2. Advanced Threat Mitigation: Beyond ransomware, iDefender is equipped to counter advanced persistent threats (APTs). It utilizes sophisticated techniques to thwart complex attack vectors such as shellcode injection and unauthorized remote access attempts. Furthermore, it addresses exploitation tactics that leverage document vulnerabilities and file-less attacks, providing a comprehensive shield against a wide range of cyber threats.
3. OS Hardening: To enhance system integrity, iDefender employs OS hardening techniques. It effectively manages persistence mechanisms and high-risk behaviors, reducing potential attack surfaces and thereby reinforcing overall system security against intrusions.
4. Blocking Unauthorized Access: iDefender prioritizes user privacy and data security. It implements multiple protective layers to conceal sensitive information and intercept unauthorized access attempts. Features such as file hiding and stringent access controls significantly minimize the risk of data breaches, ensuring confidentiality for both personal and professional information.
5. Productivity Enhancement: The software is designed to improve user productivity by efficiently managing system resources. iDefender prevents unnecessary processes and services during startup, which helps maintain optimal device performance. This allows users to focus on their tasks without the distraction of system slowdowns.
Conclusion
For individuals seeking a powerful and user-friendly security solution, iDefender 5.2.2.0 is an exceptional choice. It offers formidable protection against a diverse range of threats, including ransomware and sophisticated cyber attacks, while ensuring a smooth user experience. With iDefender safeguarding your devices, you can navigate the digital landscape with confidence, knowing that your security is in capable hands.
Future Developments and Considerations: As cyber threats continue to evolve, ongoing updates to iDefender will be crucial in maintaining its effectiveness. Users should remain vigilant about software updates and consider complementary security measures to further enhance their device protection
Key Features of iDefender
1. Ransomware Protection: iDefender excels at combatting ransomware attacks. It detects and blocks these threats in real-time, protecting critical files from malicious encryption attempts. Its advanced detection mechanisms allow it to monitor for suspicious activities that may indicate unauthorized encryption, ensuring that valuable data remains uncompromised.
2. Advanced Threat Mitigation: Beyond ransomware, iDefender is equipped to counter advanced persistent threats (APTs). It utilizes sophisticated techniques to thwart complex attack vectors such as shellcode injection and unauthorized remote access attempts. Furthermore, it addresses exploitation tactics that leverage document vulnerabilities and file-less attacks, providing a comprehensive shield against a wide range of cyber threats.
3. OS Hardening: To enhance system integrity, iDefender employs OS hardening techniques. It effectively manages persistence mechanisms and high-risk behaviors, reducing potential attack surfaces and thereby reinforcing overall system security against intrusions.
4. Blocking Unauthorized Access: iDefender prioritizes user privacy and data security. It implements multiple protective layers to conceal sensitive information and intercept unauthorized access attempts. Features such as file hiding and stringent access controls significantly minimize the risk of data breaches, ensuring confidentiality for both personal and professional information.
5. Productivity Enhancement: The software is designed to improve user productivity by efficiently managing system resources. iDefender prevents unnecessary processes and services during startup, which helps maintain optimal device performance. This allows users to focus on their tasks without the distraction of system slowdowns.
Conclusion
For individuals seeking a powerful and user-friendly security solution, iDefender 5.2.2.0 is an exceptional choice. It offers formidable protection against a diverse range of threats, including ransomware and sophisticated cyber attacks, while ensuring a smooth user experience. With iDefender safeguarding your devices, you can navigate the digital landscape with confidence, knowing that your security is in capable hands.
Future Developments and Considerations: As cyber threats continue to evolve, ongoing updates to iDefender will be crucial in maintaining its effectiveness. Users should remain vigilant about software updates and consider complementary security measures to further enhance their device protection
iDefender 5.2.2.0 released
iDefender is a cutting-edge security solution designed for home use, offering both an Intrusion Prevention System (HIPS) and Real-time Endpoint Detection and Response (EDR). This integrated system protects against potential threats, ensuring the safety and integrity of your devices by actively monitoring and responding to suspicious activities.