HTTP Toolkit has released version 1.22.1, enhancing its capabilities for automatic interception of HTTP and HTTPS traffic across a wide range of clients. This tool is compatible with major web browsers like Chrome and Firefox, command-line interface (CLI) tools, and back-end programming languages including Node.js, Python, and Ruby. HTTP Toolkit functions as an HTTP(S) proxy, making it versatile for platforms that lack built-in integrations.
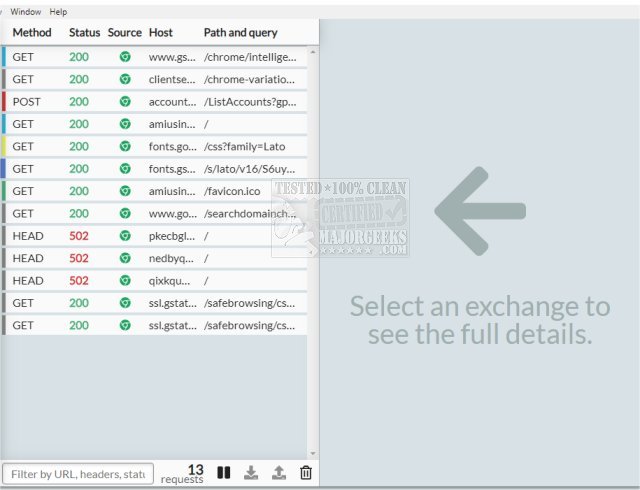
One of the standout features of HTTP Toolkit is its ability to organize and analyze traffic efficiently. Users can filter traffic based on content type, status, and source, or conduct targeted searches using URLs, statuses, and headers to locate important messages. The tool provides detailed insights into each request and response, displaying URLs, statuses, headers, and bodies with inline explanations and documentation sourced from MDN (Mozilla Developer Network).
Moreover, HTTP Toolkit leverages the power of the Monaco editor from Visual Studio Code, allowing users to explore message bodies with advanced highlighting and autoformatting for various formats such as JSON, HTML, JavaScript, and hexadecimal.
Another key feature is the ability to pause and edit live HTTP traffic. Users can precisely match requests as they surface, allowing for modifications to the target URL, method, headers, or message body. Additionally, the tool supports manual responses to incoming requests, enabling users to either manipulate the responses on the fly or pass them upstream for further processing.
HTTP Toolkit is designed to function seamlessly across multiple operating systems, including Linux, Mac, and Windows. It encompasses all essential HTTP debugging features and provides manual HTTP mocking and rewriting capabilities.
In summary, HTTP Toolkit 1.22.1 is a powerful, cross-platform tool for developers and testers, streamlining the process of HTTP debugging and traffic analysis with its intuitive interface and comprehensive features. As the tool continues to evolve, it promises to enhance the efficiency and effectiveness of web development and testing workflows. Users can expect regular updates and improvements, making HTTP Toolkit an invaluable resource for handling HTTP traffic
One of the standout features of HTTP Toolkit is its ability to organize and analyze traffic efficiently. Users can filter traffic based on content type, status, and source, or conduct targeted searches using URLs, statuses, and headers to locate important messages. The tool provides detailed insights into each request and response, displaying URLs, statuses, headers, and bodies with inline explanations and documentation sourced from MDN (Mozilla Developer Network).
Moreover, HTTP Toolkit leverages the power of the Monaco editor from Visual Studio Code, allowing users to explore message bodies with advanced highlighting and autoformatting for various formats such as JSON, HTML, JavaScript, and hexadecimal.
Another key feature is the ability to pause and edit live HTTP traffic. Users can precisely match requests as they surface, allowing for modifications to the target URL, method, headers, or message body. Additionally, the tool supports manual responses to incoming requests, enabling users to either manipulate the responses on the fly or pass them upstream for further processing.
HTTP Toolkit is designed to function seamlessly across multiple operating systems, including Linux, Mac, and Windows. It encompasses all essential HTTP debugging features and provides manual HTTP mocking and rewriting capabilities.
In summary, HTTP Toolkit 1.22.1 is a powerful, cross-platform tool for developers and testers, streamlining the process of HTTP debugging and traffic analysis with its intuitive interface and comprehensive features. As the tool continues to evolve, it promises to enhance the efficiency and effectiveness of web development and testing workflows. Users can expect regular updates and improvements, making HTTP Toolkit an invaluable resource for handling HTTP traffic
HTTP Toolkit 1.22.1 released
HTTP Toolkit offers automatic interception of HTTP and HTTPS traffic from most clients, including web browsers like Chrome and Firefox, almost all CLI tools, and back-end languages (Node.js, Python, Ruby, and more).